According to Wikipedia:
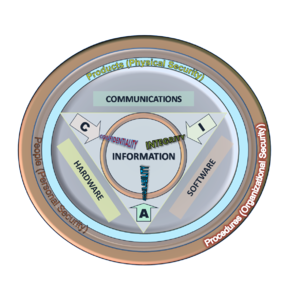
“Information security (sometimes shortened to InfoSec) is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take.”
In non-legalese terms, infosec includes:
- Confidentiality (protected from unauthorized access)
- Integrity (protected from unauthorized changes)
- Availability (there when it’s supposed to be)
It helps to approach infosec in layers, focusing on the integration points between each layer, or attack vector. Since integration points have to expose data in order to share information, they are likely targets for attack. Those attack vectors include:
- Applications
- Endpoints
- Networks
- Servers
- Data
- Locations
- People
The concept of implementing controls at each of these integration points is often referred to as defense in depth.
For more information on how to protect each of these layers, check out the Common Sense Security Framework.
A step-by-step process for implementing information security controls is as follows:
- Identify the data (i.e., document a dataflow diagram)
- Identify each asset that the data resides on (data at rest)
- Identify each asset that the data passes through (data in motion)
- Identify all applications that touch the data (including backups)
- Identify user access stores and models for everyone who can see and/or modify the data
- Identify vulnerabilities at each step of the dataflow process
- Attempt to exploit those vulnerabilities
- Implement controls to remediate (or at least mitigate) those vulnerabilities
Remember: there’s a way around every control. As an information security professional, it’s your job to identify and implement reasonable controls that are sufficient to deter attackers.